TSN is comprised of several standards that are specified in the IEEE 802.1 and 802.3 working groups. Parts were already launched, others are still in preparation. The newly introduced technology poses additional requirements for a network. These include the availability of a common time base. The shared understanding of time across all devices is necessary in order for data frames to be able to be transferred deterministically, meaning a clearly defined time limit for end-to-end latency (delay time) and low jitter (delay fluctuations).
For deterministic data transfer in TSN, time will be divided into periods by means of the TDMA (Time Division Multiple Access) method. Within these periods, time slots for data streams are reserved. This creates virtual channels from one terminal device connected to the network to another. These channelsare closely linked to the internal clocks of the participating network members. In order to achieve high precision for time synchronization, TSN usually uses the Precision Time Protocol (PTP) in accordance to IEEE1588.
Time as an Attack Vector
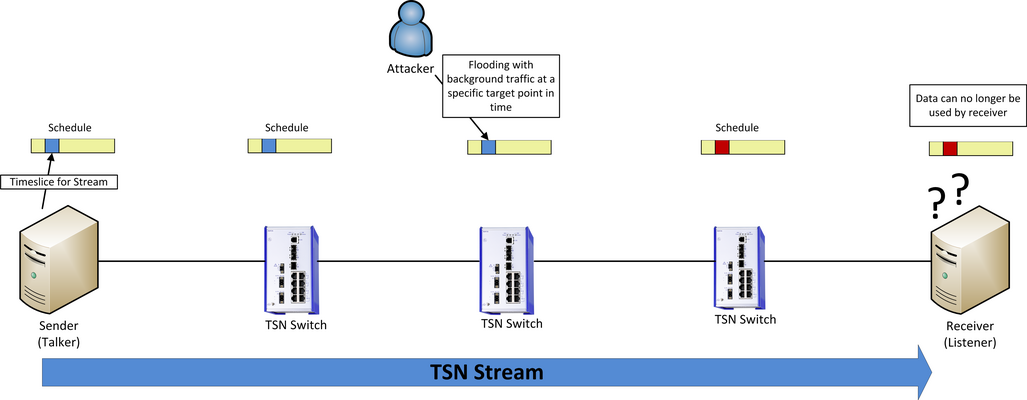
In order to attack Ethernet networks commonly used today, denial of service attacks (DoS) are a widely used tool. DoS attacks flood the network with data until it is overloaded. Since TSN is based on the availability of time data, both the PTP protocol as well as the TDMA method expose new attack vectors. For example, for a DoS attack on TSN, it is already enough to deliberately overload a single time slot.
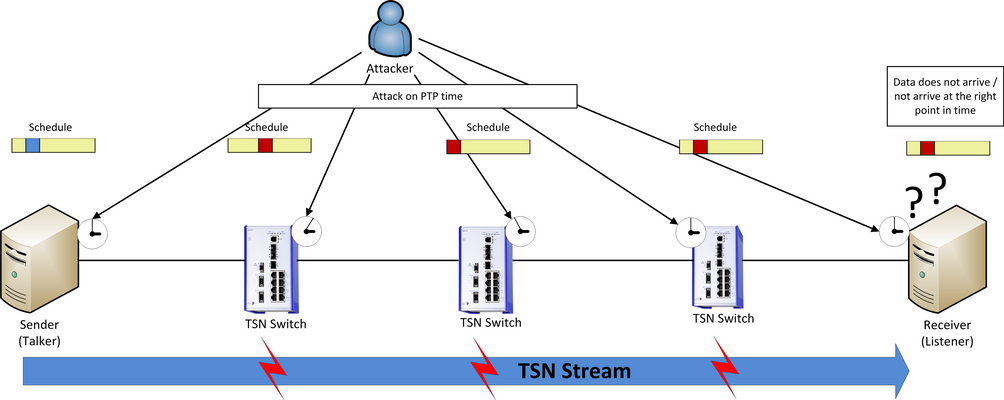
Besides the targeted overloading of certain time slots, the protocol IEEE1588 for time synchronization is also a potential attack target.
Many automation networks today already use PTP. For this reason, it will be utilized in many applications for the synchronization of TSN clocks. PTP itself has no integrated security mechanism and relies completely on the security mechanisms present in the network.
Without network security, a potential attacker could capture the functions of the central time source, the "Grandmaster," with falsified PTP data packets and bring false time information into the network, which could impair the use of TSN.
What does this mean for the cyber security of TSN networks?
Network Protection
Besides its target for attack, the timing aspect also impacts the application of certain security measures. If firewall data packets cannot be checked in real time because the software has to look into the load capacity (Deep Packet Inspection, DPI), this creates a delay in the transmission. If this is not taken into consideration from the start, it will create a conflict between data and time slots for which they were not intended. One possibility for getting on top of this issue are firewall technologies that filter in real time. Another possibility is to make the additional delay transparent in the network, so that the calculation of the TDMA method schedule can be integrated.
Depending on the application requirements, even if it's made visible, a long delay cannot potentially be tolerated. Thus, two different situations need to be distinguished: on the one hand, mechanisms that are directly situation inside the TSN communication path, and, on the other, mechanisms on the boundaries of a TSN communication path. Security mechanisms on the communication path may only show a low additional transfer latency. However, delays on the boundaries of the communication path may frequently be tolerated.
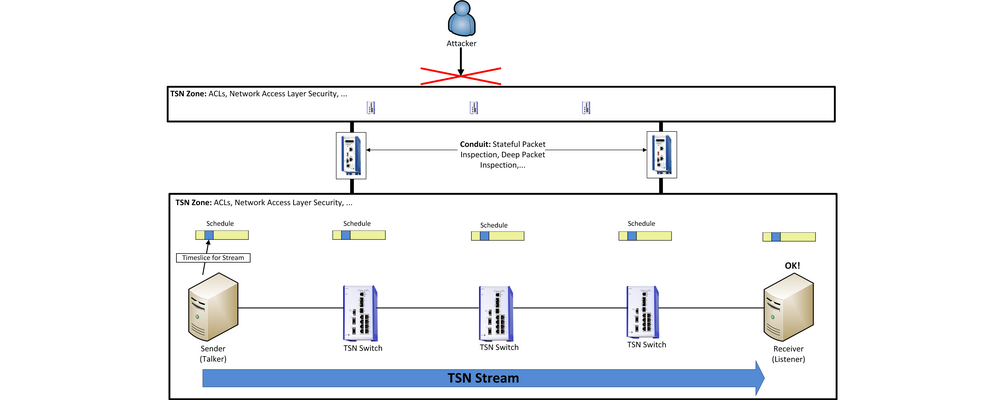
This approach corresponds to established approaches of zones and and conduits and adds an additional TSN aspect to this method. The subdivision of a network into communication zones serves to separate areas from each other and to allow only strictly necessary communication. Until now, this approach only applied to cyber security. Along with this approach for communication needs (the need to communicate) the additional level of time requirements (the timing of communication) comes up in TSN networks.
This way, besides zones and conduits, another established security concept is implemented at the same time, namely "Defense in Depth and Diversity". This concept, which is designed as an in depth defense, various security mechanisms are connected in series. On one side, there are the classic security mechanisms on the network access level (Network Access Layer Security), such as IEEE802.1X, that are implemented in switches and routers that protect the direct access to the TSN net. On the other side, mechanisms are also prepared for this purpose in the TSN specification.
Layer 2 Security
To prevent attacks on level 2 of the OSI layer model, measures are already in the planning stages in TSN standardization. One of these is Ingress Filtering and Policing, which is specified in the prospective IEEE-Standard P802.1Qci. In this process, the data packets are checked for whether they fit to a reserved data stream at the network input. If this is not the case, the packet will be filtered out and rejected. Additionally, mechanisms such as MACsec (Media Access Control Security) can be used, which allows data streams between two network members to be encrypted.
Security for the configuration and the tools
The integral components of a functioning TSN network are not only the network devices themselves, but also the mechanisms for configuration of devices and communication streams. In the IEEE 802.1 TSN work group, within the framework of the work on the future Standard IEEE P802.1Qcc, three different configuration concepts are currently being considered: Completely decentralized, completely centralized, and a hybrid of centralized and decentralized communication. Especially in regards to the communication with network devices, it must be made sure that the connection to the devices and the configuration by a user are subject to security limitations normally used today. Reliable security measures, like a role-based access with security credentials, such as user name and password, but also further procedures like two-factor authentication, must be implemented to authorize the buildup or teardown of a TSN communication stream as well as the authorization to change the configuration of devices. In conclusion, an established, active TSN communication stream is an asset worth protecting, just like a TSN Switch or an end device.
Summary
TSN is the universal advancement of Ethernet technology. The high bandwidth and real time services that this new standard can do provide the prerequisite for the modern automation networks of the future. The wheel does not have to be reinvented in order to guarantee cyber security in TSN networks. The security mechanisms used in the industry today are absolutely sufficient, even though the strict demand for real time adds a new aspect. This fits, however, seamlessly into existing concepts.
Authors: Dr. René Hummen and Dr. Oliver Kleineberg